What is PAM?
Privileged Account is an account that has high privileges on systems, networks, and applications. It controls the entire IT infrastructure of a company, including system configuration changes and access to critical data. Its unauthorized use can lead to significant security incidents. Such unauthorized use not only causes serious damage to business operations but also carries risks of legal penalties and heavy fines, so strict control over the use of privileged IDs is required.
This control is implemented through a mechanism known as Privileged Access Management (PAM). By restricting access rights to the minimum necessary, and closely monitoring and recording usage, PAM ensures that it is always clear who did what and when.
However, in practice, there are many cases where management relies heavily on individual discretion, and errors caused by the enormous workload of Privileged Access Management frequently occur. In ASEAN countries, such “invisible operations” pose an increasing risk of causing serious management issues.
Security Risks Lurking in Thai Bases
At the Thailand offices, while IT adoption and cloud usage are progressing, access management and data protection often remain manual and reliant on individual discretion. Furthermore, due to low employee awareness of security measures and insufficient training,there is a heightened risk of insider threats.
In addition, Thailand experiences an average of 3,180 cyberattacks per week, which is 1.7 times the global average (2024, Check Point Research), making it one of the highest-risk regions in Asia for external attacks. Internal breaches are particularly prominent, and in environments where Privileged Access Management (PAM) is not functioning effectively, detection of anomalies is delayed, increasing the likelihood of severe risks.
The management of privileged IDs should be reconsidered not merely as a security measure but as a starting point for strengthening governance.
Why iDoperation Stands Out as the Leading Japan-Made PAM Solution
iDoperation, developed by NTT-TX, is a PAM tool that has held the No.1 market share in Japan for 12 consecutive years (according to Fuji Chimera Research Institute). It automates and provides full visibility into all stages of privileged ID management, including management, usage, and inspection, thereby removing manual, person-dependent operations and creating a streamlined and effective PAM environment.
Moreover, iDoperation complies with Japan’s stringent audit and security standards such as J-SOX, ISMS, and FISC, which is a major reason why companies in any country can use it with confidence. By implementing iDoperation, organizations can ensure world-class security standards and easily unify internal controls across different countries.
Currently, the service is available not only in Thailand but also in Indonesia and Hong Kong, with plans to launch in Singapore and Malaysia. As corporate awareness and demand for PAM increase, iDoperation is expected to further expand its service area.
YAMAHA’s Use Case
Background: Maintaining IT General Controls is a pressing challenge in the face of evolving business environments. Yamaha Motor Co., Ltd., which develops, manufactures, and sells a diverse range of products including motorcycles, boats, electric-assist bicycles, and various industrial robots, continues to grow. Since 2009, the company has introduced and operated a PAM solution to comply with the internal controls required by the Japanese version of the SOX Act (J-SOX), specifically for audits of “IT General Controls.”
Selection: The deciding factor for adoption was iDoperation’s support for the client-based model and its high scalability, which does not disrupt the existing environment.
Mr. Wada(*1) explained that the key reasons for adoption were not only the proven track record in strengthening controls such as internal control and J-SOX audits but also the fact that access to the production servers is not concentrated through a single gateway. Instead, it can be used in a client-based manner (a method that controls access directly from the client to the server) (see Figure 2). Additionally, being a Japan-made solution provided a sense of security regarding support.
“Since the company operates globally, we do not necessarily insist on domestic products. However, J-SOX audits also cover overseas subsidiaries. Another important factor was the
capability to rapidly expand overseas if required, while leveraging domestic expertise and receiving the dedicated support that only local solutions can provide.” (Mr. Wada)
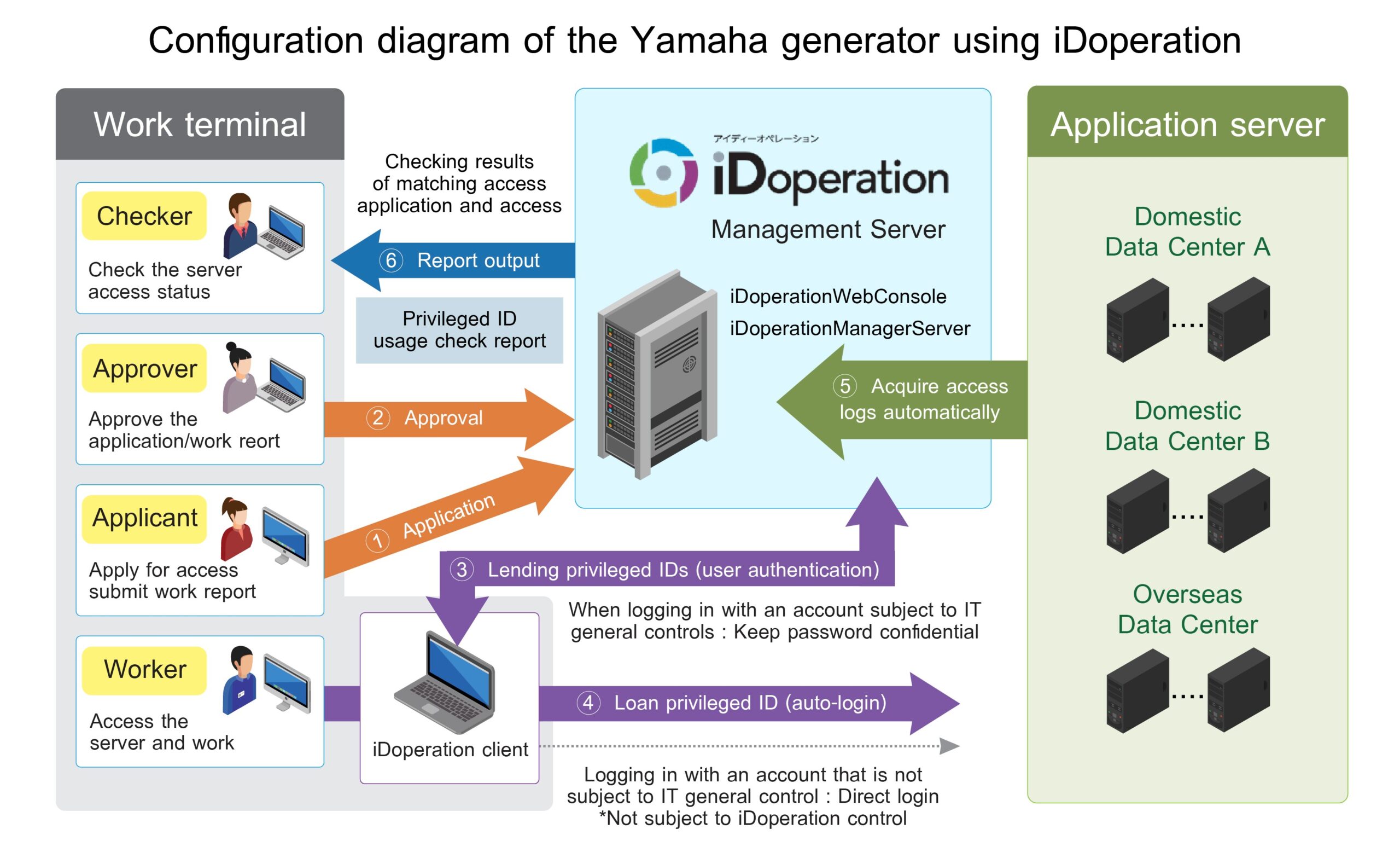
Effects: Strengthening of overall IT general controls, reduction of infrastructure operation workload, and improvement of security levels have been achieved.
As an effect that has already begun to appear, the most highly evaluated point is that “even after switching tools, the system to maintain the previous control activities has been preserved” (*2).
In addition, iDoperation has a function that automatically cross-checks privileged ID usage requests with user access logs to servers to detect any unauthorized access. This provides practical benefits during audits and, from the perspective of the operations team’s countermeasures against unauthorized access, Mr. Oda (*3) explains that it “leads to improvements in security.”
Future Plans:
With a view to addressing personal information protection and security requirements, the scope of servers targeted for iDoperation implementation will be expanded.
The introduction of iDoperation has strengthened the transparency and visibility of Privileged Access Management. Regarding future prospects, Ms. Wada stated, “We plan to expand the servers managed by iDoperation and also consider compliance with personalinformation protection requirements.”
Conclusion
Even companies that have introduced PAM (Privileged Access Management) may face risks when actual operations become a black box, failing to fulfill accountability to management and auditors.
iDoperation, backed by extensive experience in Japan, is a tool that helps build a system to clearly understand “who did what and when,” supporting both control and management at offices across ASEAN countries. Now, returning to the “basics” of privileged ID management is the first step toward preparing for future risks. It may be a good idea to start by gathering information, including whether or not to implement the solution.
Review our solution at https://magicsoftware.co.th/idoperation/
For product inquiries, please contact:
Magic Software (Thailand) Co., Ltd.
Email: sales.cybersec@magicsoftware.co.th
 The Business Plus บิสิเนสพลัส
The Business Plus บิสิเนสพลัส



